CASCADE R&D is supported by funds from several funding agencies, including NSF and DOE, as well as various industrial partners.
CRY3CON: Assessing Supply-chain Risk with Darkweb Data
CRY3CON is a cybersecurity firm based in Arizona, which was created to commercialize recent Arizona State University research efforts in artificial intelligence and cybersecurity. CRY3CON is unique in the way in which the firm predicts cyber attacks by using advanced machine learning techniques, and mathematical analysis of hacker social structures in data mined from hacker communities on the dark web. The firm provides proactive cybersecurity capabilities to customers through a SaaS-based platform sold as a subscription either directly to customers or through a security provider. Along with some of the firms 2017 results being covered by both CNN and the Economist, CRY3CON has been either awarded or been a finalist in over ten different data science and cybersecurity-related competitions in the last two years.
CRY3CON has partnered with ASU personnel to address the ongoing issue of cyber attack risk associated with third-party vendors in a supply chain. Currently, firms lack the ability to closely examine and monitor the IT infrastructure of at-risk third-party vendors. CRY3CON seeks to support their clients by giving them the ability to monitor threats of cyber attacks to third parties through the use of dark web hacker information. However, the problem CRY3CON faces are that any given client may have hundreds of third parties which would require the processing of thousands of suspicious conversations in order to identify at-risk third-party vendors and understand their threats. CYR3CON has decided to partner with ASU to leverage their expertise in dark web mining in order to automate the identification of threats to third-party vendors in a scalable manner. Lead by the principal investigator Ph.D. Paulo Shakarian, a Fulton Entrepreneurial Professor at ASU and CEO of CRY3CON, the project of interest was created.
The goal of the project entitled; Assessing Supply-Chain Risk with Dark Web Data is to develop/enhance techniques to identify “at-risk” third parties for triage, develop analytical methods to understand shifts in hacker conversations and changes in conversation with respect to certain third parties over time, and to create/adopt big data search and indexing to allow for rapid search through hundreds of sources. The research will include proof-of-concept(s) using technologies for vendor risk management, visualization of results in a way that is intuitive and meaningful for end-user analysts, evaluation of algorithmic approaches in terms of runtime and ability to proceed cyber attacks, evaluation of algorithmic approaches based on real-world feedback from experts provided by CYR3CON, and data sets assessments for proof-of-concept(s) including: those provided by sponsors within the federal government.
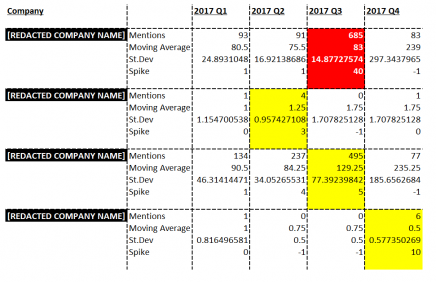
The project is broken up into three stages, the first stage is set to develop statistical and unsupervised machine learning techniques to identify at-risk third-party vendors. This stage is intended to use more robust methods of identifying periods that are of high cyber attack risks. The second stage is evaluating the high-risk period (see figure above) and coming up with a simple visualization of the hacker conversations (see figure below) that can provide insight into the risks posed to vendors. An expected challenge within the second stage is the dark webs multilingual communication and common use of slang, which makes it harder to identify conversations of interest. In the third stage, researchers seek to support the results of the topic distribution with tools such as Lucene and Elastic Search. They plan to leverage the methods from stage two to in order to automate the integration of results into the visualizations provided to CYR3CON.

In summary, CYR3CON will work with ASU personnel on the project: Assessing Supply-Chain Risk with Dark Web Data and use real-world client data to benchmark techniques for triage of third-party vendors and leverage topic modeling to mine for key risk information regarding these vendors. The assessment of the risk data will be evaluated using multiple means – with a particular focus on indicators preceding cyber attacks and expert evaluation. As the projects are ongoing, results will be published following the conclusion of the final project milestone.